Topics
February 23, 2018
Cybersecurity Steps to Avoid Storms in the Cloud

2017 was one of the worst years in regards to data loss. According to a report by the Online Trust Alliance (OTA), security incidents have doubled from 82,000 in 2016 to 159,700 in 2017. What’s more alarming, according to the report, is that 93% of the breaches could have been prevented with better cyber hygiene. The cloud is one area that is gaining more attention—and an area that isn’t immune to cyber-attacks.
A technique that grabbed attention in 2017, called GhostWriter, is a method for attackers to replace benign files with malicious code in Amazon S3 buckets. Often, the technique was used to facilitate drive-by attacks, crypto coin mining, or other attack methods. Put another way, your cloud website could be serving up malware that is being used to attack your customers, or your systems are being used to make other people money by allowing them to calculate functions that result in someone else’s crypto wallet getting fatter. Overall, your brand could be damaged and your customers might take their business elsewhere.
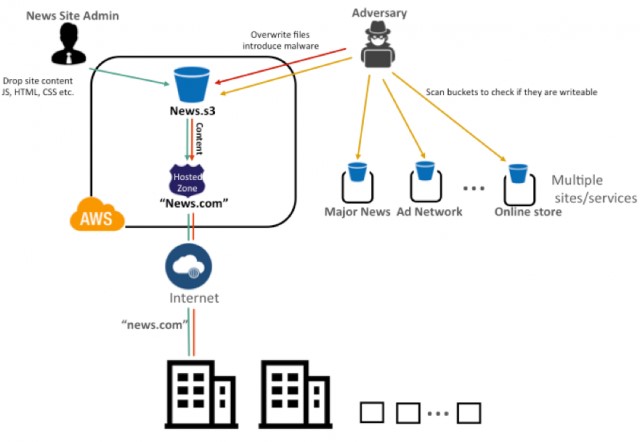
Figure 1. GhostWriter Attack on a Cloud Environment.
Whether your organization’s systems are hosted in-house, or the cloud, security cannot be an afterthought. When considering a move to a cloud environment, cyber security hygiene will need to be one of first topics of conversation. Like any system, the cloud presents a unique set of security challenges, while enabling new conveniences and opportunities for business.
Public, Private and Hybrid Clouds
Your organization may have already embraced the cloud, without looking back. Others, may have reservations about what the cloud really means, while some may have been using the cloud without even realizing it.
What is the cloud? It is essentially someone else’s computer. Although this may not be that surprising, the means to secure a cloud environment are different. All clouds are not equal, and it is helpful to understand the variations out there. In general terms, there are three types: public, private and hybrid. There are other categories, but suffice it to say that these are the most common.
A public cloud is the collection of systems, applications and infrastructure that is shared with others and typically in a 3rd party data center. If you have a web-mail system like Gmail, you are using a public cloud system.
Private clouds exist in a similar manner; however, the systems, infrastructure and applications are not shared. In many cases the private cloud is connected back to an organization’s on-site systems and acts as an extension, or force multiplier, for an organization. This can be very beneficial for an organization that may not have the physical resources to create or expand their own data center. For example, you don’t have the money to pay for a data center, so you have a private area in the cloud carved out for you. Amazon Web Services (AWS) has this option, which usually just means that your systems are in the cloud, but not accessible to the rest of the world.
Finally, the hybrid cloud consists of a combination of both public and private aspects.
Benefits of Leveraging the Cloud
There are many reasons for leveraging the cloud, which can include business enablement and capability that wouldn’t exist in a traditional data center, or at least without significant hardware spend and support costs. The top benefits include:
- Rapid development and deployment of systems
- Reduces hardware and data center costs
- Accessibility of systems
- Redundancy and system scalability
- Monitored infrastructure
This list is not comprehensive, but it represents some of the benefits and appeal of moving to a cloud model. Moving to the cloud, however, can present challenges and new costs.

Challenges of the Leveraging the Cloud
It’s not all cirrus (usually non-storm producing) clouds when it comes to a cloud environment. As stated before, cloud systems are just systems hosted by a third-party, with varying degrees of public accessibly. Some of the challenges to consider are as follows:
- Network Intrusion Detection (IDS) blind spots
- Support with the 3rd party management applications
- Vulnerability and patch management
- Incident Response
- Security Assessments and penetration tests
- Learning curve (if your existing team is tasked with moving existing systems to the cloud)
- Unrealized costs from unnecessary systems
- Cyber Hygiene i.e. how do you apply the same controls to this environment.
- Does the cloud environment conform to your regulatory requirements?
Because the infrastructure is not owned by the organization, there are additional considerations to take into account when considering security for a cloud-based environment. One example is that of an external vulnerability or penetration test. Approval to test the security of the systems is required to go through the 3rd party. This can be delayed if there are shared systems in the test, such as a Domain Name System (DNS) server. Some organizations have made a one-for-one switch to the cloud only to realize that the costs were significantly higher. These costs may have been from unnecessary systems or from compute costs that were never factored in, or had to be considered previously.
Security Tools and Resources
Depending on the third-party cloud provider, there exist many tools for securing the environment and keeping up with cyber hygiene. In the case of AWS, these tools are even provided directly from Amazon (at an additional cost in some cases). Other vendors provide a cloud version of their tools that can interface with the cloud provider. From vulnerability and configuration assessments, to identify and access management, there are many of the same functions that would be available to an organization with on-site assets. If you are migrating to the cloud, having a familiar set of tools may make the transition seem less overwhelming.
Future Trends
The future is bright for the cloud. From growth, to new services and offerings, the writing is on the wall. In terms of security, and as the popularity of the service rises, attacks and challenges will also grow. It’s important to not get lost in the complexity. Because the cloud is just a third-party system, it can be secured with similar principles of confidentiality, integrity and availability that an on-premise system would require. Security services are on the rise as well. These services should be considered when looking into migrating or creating new systems in a cloud environment. If your system is net new and will leverage the cloud, build security in from the start. One such guide is the Cloud Security Alliance Control Matrix, which is a great place to begin. Don’t wait until the system is built then start thinking about security.
Conclusion
With the benefits and convenience that the cloud brings, it is becoming difficult to ignore its power. Before jumping to any version of the cloud i.e. public, private or a hybrid configuration, a risk assessment and review of the available services is required to fully understand the benefits and challenges this environment presents. Armed with knowledge, navigating the cloud and its security challenges may enable your organization to outperform the competition in ways that may have otherwise been cost prohibitive in a traditional datacenter deployment.
If you're thinking of moving to the cloud, or already there, and need an assessment of your security vulnerabilities, read more here: Security Breaches: What can SMBs do to prevent and respond?
Matt Hosburgh is a passionate security practitioner, currently working as a Cyber Threat Hunter. He has over 14 years of experience in a variety of security disciplines, which includes experience supporting systems and networks for the Intelligence Community and as a Senior Security Analyst for United States Citizenship and Immigration Services (USCIS). Matt holds a graduate degree from the SANS Technology Institute, and maintains several GIAC Certifications, to include the GSE.