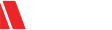Topics
How to Identify a Malicious Email: 6 Tips

Cyber-attacks can take many forms including attachments that when clicked install a virus, Trojan, or other malware on your computer; links that take you to a webpage that installs malware on your computer; and phishing email that tricks you into providing personal information such as User IDs, passwords, and account numbers to imposters pretending to be trusted companies and sites. Email spam filtering is far better than it used to be, but the best way to defend yourself is to be alert to potential fraud and know how to spot a malicious email. Below is a list of basic safeguards you should know and practice before opening email messages and attachments.
1. Outlook may detect a message is unsafe or a potential phishing email with a warning message. Do not disregard this warning!
Note: A phishing email is a scam attempt in which a criminal claims to be a reputable establishment in an effort to lure a victim into handing over private information.
2. Does the subject line or body of the email seem out of character or unusual given the sender, especially if you are not expecting an email from that organization or person? Think twice (or three times) about this!
A common phishing email comes in the form of an email from the IRS alerting you about an error in Tax filing, and urging you to take action in some way. We will use the IRS as our primary example to illustrate this point.
First, if you see an attachment, delete the message immediately. Legitimate IRS emails (as well as those from many other organizations including banks) are for notification purposes only and will never include attachments.
Second, go to the IRS home page and search on the letter, notice, or form number. Fraudsters often modify legitimate IRS letters. You can also find information at Understanding Your Notice or Letter or by searching Forms and Pubs.
Third, send IRS the email or scanned fax via email to [email protected] (Subject: 'FAX').
This document from IRS provides a variety of examples of fraud emails to look out for.
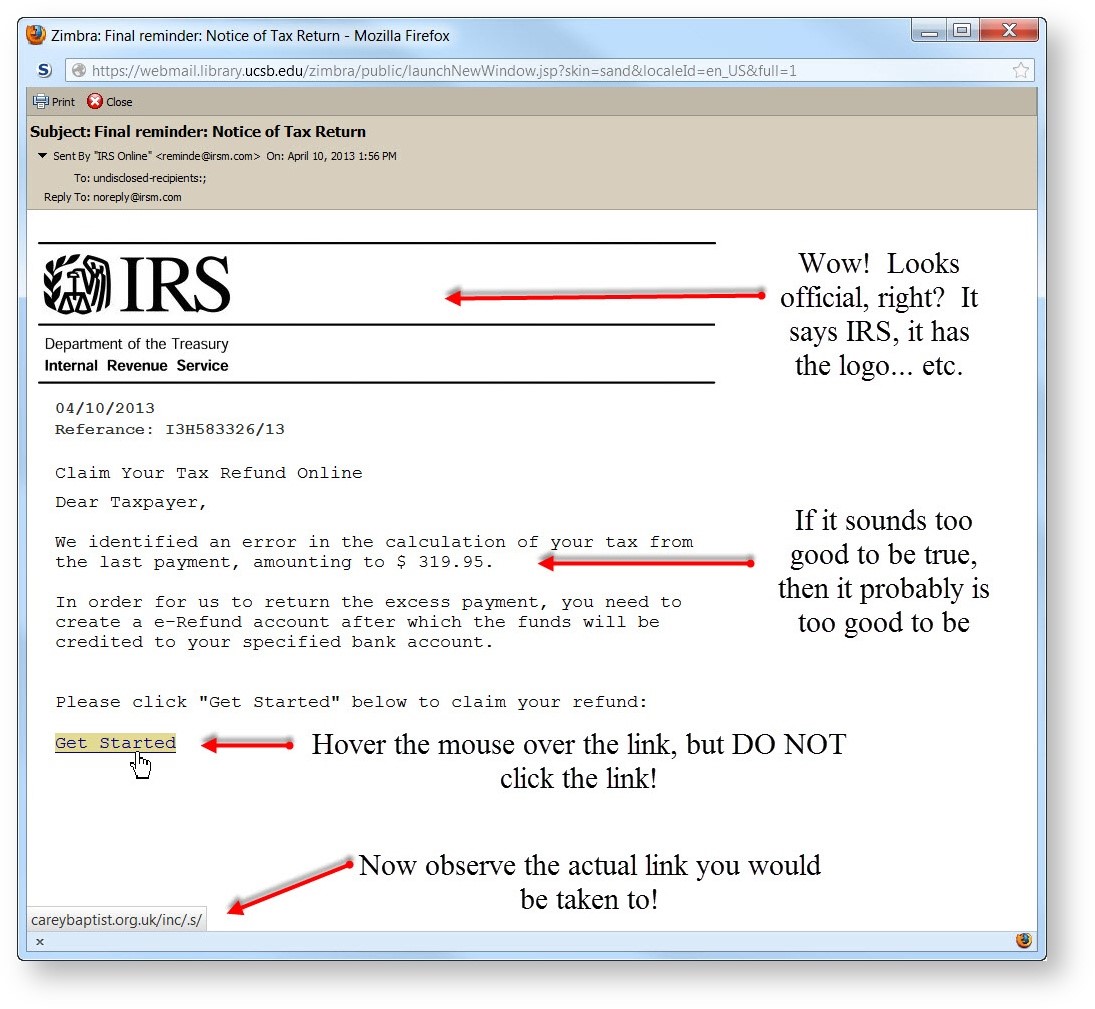
3. Always check hidden links if you are urged to unlock an exciting offer, view your account, etc. by clicking a hyperlink.
Scroll your mouse (without clicking) over the hyperlink to reveal its real address – if you see something strange or unexpected (think a lot of random numbers, letters, a strange domain you’ve never heard of, etc.), delete the email right away.
- In all cases, it is always better to log in to your accounts (banking, mortgage, online retailers, etc.) online rather than doing so through an email.
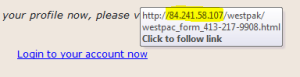
4. Are you being urged to log in to an account by clicking a link? Are you being threatened in any way if you don’t act quickly?
Some examples may be “log in to your account now before…” or “you will be charged unless you act now,” etc. Any statement which urges you to act by clicking a link or opening an attachment should raise a red flag. If you want to check an account, navigate to the appropriate website via your internet browser and log in this way.
The below image shows a phishing email cleverly disguised as a friendly message from Chase bank. In this case, the recipient should navigate to www.chase.com and log in the old-fashioned way in order to check the status of his/her account.
5. Browse to the sender's website directly. Do this by manually entering the Web address root in a Web browser address bar. Then use the website's navigation to find the information referred to in the email message.
If the email message was legitimate, the contents will be available at the website too.
Tip: When browsing, check the browser's address bar for the correct institution's address -- for example, XYZ Bank. Even if the Web address has the bank's name in it, it may not be the bank's website. For example, XYZBankSecure.net, is not the same as XYZ Bank.com
Warning: Never enter bank login details after following an emailed link. Always log in to the bank directly from a fresh tab in a Web browser. Never enter details in pop-up windows.
If you believe your confidential information may have been stolen or obtained by a fraudulent party either online, by telephone or through any other means, contact us immediately.
6. Fake Anti-virus, Criminals send spam email and social network messages with the software installer attached, using a social engineering lure to persuade the recipient to open the attachment. Fake anti-virus, also known as rogue anti-virus or scareware, is one of the leading ways for malicious hackers to make money from unsuspecting internet users. The fake anti-virus software typically warns the user that they have various fictional security threats present on their computer. The warnings themselves are false but they are often backed up by believable descriptions of the supposed malware.
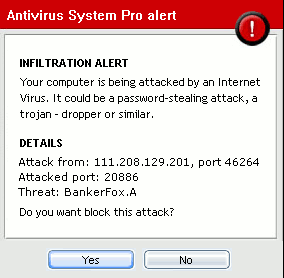
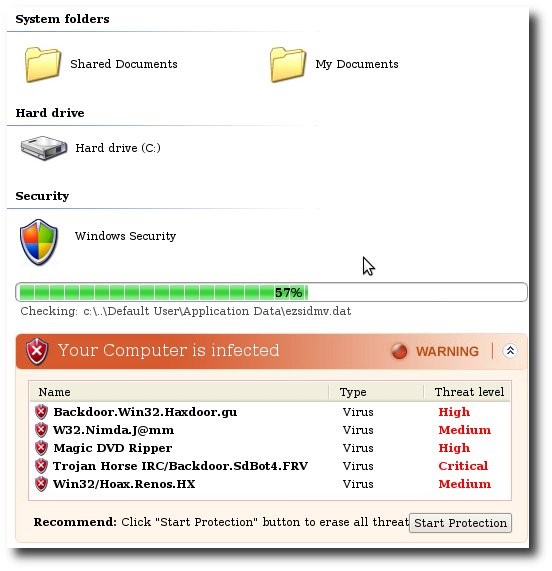
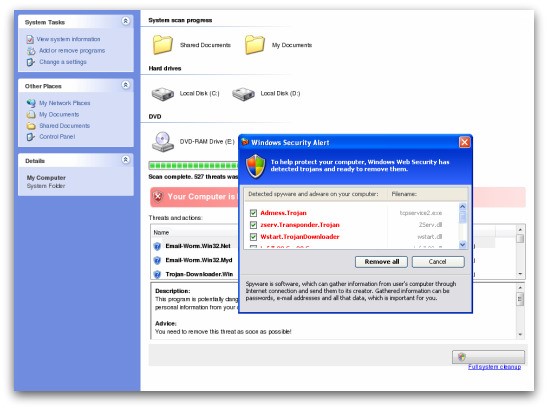
The following examples illustrate the sort of false warnings you might see on your computers:
When the user chooses to remove the threats they are asked to purchase or register the product and taken to a website that will process the payment details.
The web pages users are taken to may look like one of these:
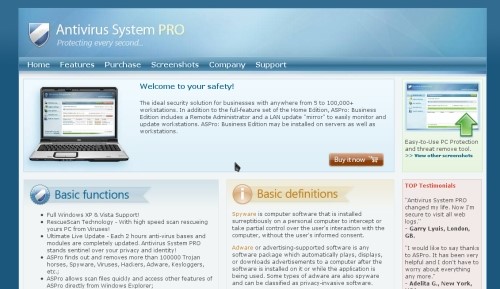
The fake anti-virus software makers use a variety of names for their software to makeit appear legitimate. Examples of these names include:
AntiSpywarePro
Antivirus Plus
Antivirus Soft
Antivirus XP
Internet Security 2010
Malware Defense
Security Central
Security Tool
Winweb Security
XP Antivirus
Always be wary of email. Even the best spam filters are only 95% effective. Unless you’re expecting a download link don’t click on one.
Most malicious pop ups are triggered by infected advertising that can appear on legitimate websites. These websites accept advertising rotations from a variety of sources that can be easy to compromise. If you’re not sure, close the window and go to the software publisher’s website to check for updates. Always better to be safe than sorry.
Furthermore, check your spam folder on a regular basis.
- Depending on your email volume, you should glance at your spam folder daily or weekly.
- Even though office 365 may learn what is and is not spam in your Inbox, it is constantly updating and tweaking its spam filtering settings.
Links and images can create problems when sending email.
- If a large volume of your email is marked as spam, make sure all of your email links are valid.
- Make sure images in your signature file have valid links as well.
Keep your messages on target and use descriptive subject lines.
- Generic subject lines (e.g., update and important) can raise your email’s spam score.
- Messages with only attachments and no body text may also be tagged as spam.
Internet security is on everyone's minds, and these six tips will help keep data and personal information safer online.