Topics
November 13, 2017
What are the motives behind cyber-attackers?

Yes, I am a criminal. My crime is that of curiosity. My crime is that of judging people by what they say and think, not what they look like. My crime is that of outsmarting you, something that you will never forgive me for.I am a hacker, and this is my manifesto. You may stop this individual, but you can't stop us all... after all, we're all alike.
–The Conscience of a Hacker From Phrack Magazine 1986, The Mentor
According to this infamous manifesto, all hackers are alike and not unique millennial snowflakes. They are people with curiosity, convictions, apathy, anger, greed, hope, and honor. Just like people, hackers or groups of hackers may fall on a spectrum of good and evil. Where they fall may be dependent on the day or mood of that individual, or even the convictions of the larger collective. For example, the collective Anonymous was a way for anyone, and I mean anyone, to be involved in hacking for an ideal if you so desired. Hate oil and gas? There was an operation for that. How about the stock market? There was Occupy Wall Street for that. What about nation states or organized crime? They might be hackers under the hood, but their motives might be considered malformed by some. On the flip side, hackers work to bring job training and technology to areas of the world that are so impoverished that they would not be able to do so on their own.

Defining Your Adversary
So maybe that’s the problem: labeling hackers as bad or good. Maybe it’s more specific than that. If you’re reading this, you’re probably wondering what the motives are behind the “bad” hackers of the world. The media does a great job classifying all hackers as bad and their motives as evil. Truly, a “bad” hacker, is subjective. It is more important to understand who your adversaries are to understand a bad hacker’s motives. This is an important differentiator for two reasons:
- An adversary implies that there is someone/somebody who has a problem with you and your organization specifically.
- An adversary helps you to understand a motive and the targets they are after.
Forming this background is one method of understanding an adversary’s motives and even the endgame.
A Motive Breeds the Target
Law enforcement often seeks to answer a common question: What was the motive? This is typically to point the investigators to the why, which can help to uncover more information or evidence to support the case and help find the criminals. Similarly, finding the why, or motive, behind your adversary’s actions can help you better understand what they are after and how to protect those assets from an attack. Take the following motives as an example:
- Financial: Can the adversary make money directly (via an attack) or indirectly (by selling malware or ransomware as a service)? Are there competitors who may want to destabilize your company?
- Ideological: Your adversary may want to harm your reputation, deny services to your customers, or sabotage your systems to further their propaganda or eliminate perceived threats to the environment, for example, this could also include frustrated ex-employees.
- Political: Can the adversary benefit from knowing your next move or most intimate secrets as an organization? Do you claim that you have impenetrable defenses? If so, you might be motivating an attacker to find a way to break through it.
- Prestige and Curiosity: Does the adversary want to say they compromised your organization just because? Do you have such an interesting technological footprint that it is enticing to an attacker?
These common motives will help you and your organization realize what could be a target and focus your budget and resources on the most vulnerable areas

All Motives Not Equal
Financial motives are among the largest reasons for targeting an organization or individual. According to estimates by Juniper Networks, the cost of data breaches will soar to 2.1 trillion dollars by 2019. This staggering statistic signals that there is money to be made. An investigative tool called Hunchly offers a service that searches the dark web and reports its findings on a daily basis. In a recent report, the following services found on the dark web relate to credit card fraud:
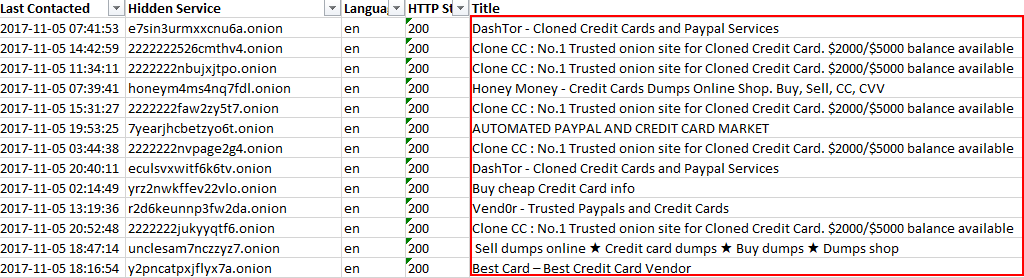
Discovered dark web services that pertain to credit cards via Hunchly.
Looking at the different site names is interesting, but also sobering. Crime is a commodity because it pays. Furthermore, an organization that may not be a target for one adversary will be one for another. Simply put, if you do not make yourself a hard target, it is only a matter of time before your organization is caught in the crosshairs.
What are they targeting?
If your adversary is financially motivated, they will more than likely be after data that can be bought and sold. In the case of ransomware, they might be after the data that you need to run your business knowing you will pay anything to get it back. A recent malware outbreak, dubbed “Bad Rabbit,” is one example where the authors were after a ransom. The target: Russian media outlets and other large corporate networks. These targets were presumably chosen because of the propensity to pay the ransom. If attackers have ideological goals, they might be looking to deny services or deface an organization’s publicly facing systems. Not knowing who your adversary is and what is motivating them is like trying to plan for a trip without knowing what the weather will be like when you get there. That translates into needing to prepare for every occasion, which is time-consuming, expensive, and nearly impossible.
Conclusion
Do you know who is targeting you and why? What are they after? These questions should be at the forefront of your mind and cybersecurity planning. Not only will this view help you look at what you’re trying to protect from the adversary perspective it will help align your strategy to meaningful priorities. When in doubt follow the money. When you’re informed, prioritize your defenses on the motives of your adversaries.
Matt Hosburgh is a passionate security practitioner, currently working as a Cyber Threat Hunter. He has over 14 years of experience in a variety of security disciplines, which includes experience supporting systems and networks for the Intelligence Community and as a Senior Security Analyst for United States Citizenship and Immigration Services (USCIS).
Matt holds a graduate degree from the SANS Technology Institute, and maintains several GIAC Certifications, to include the GSE.