Topics
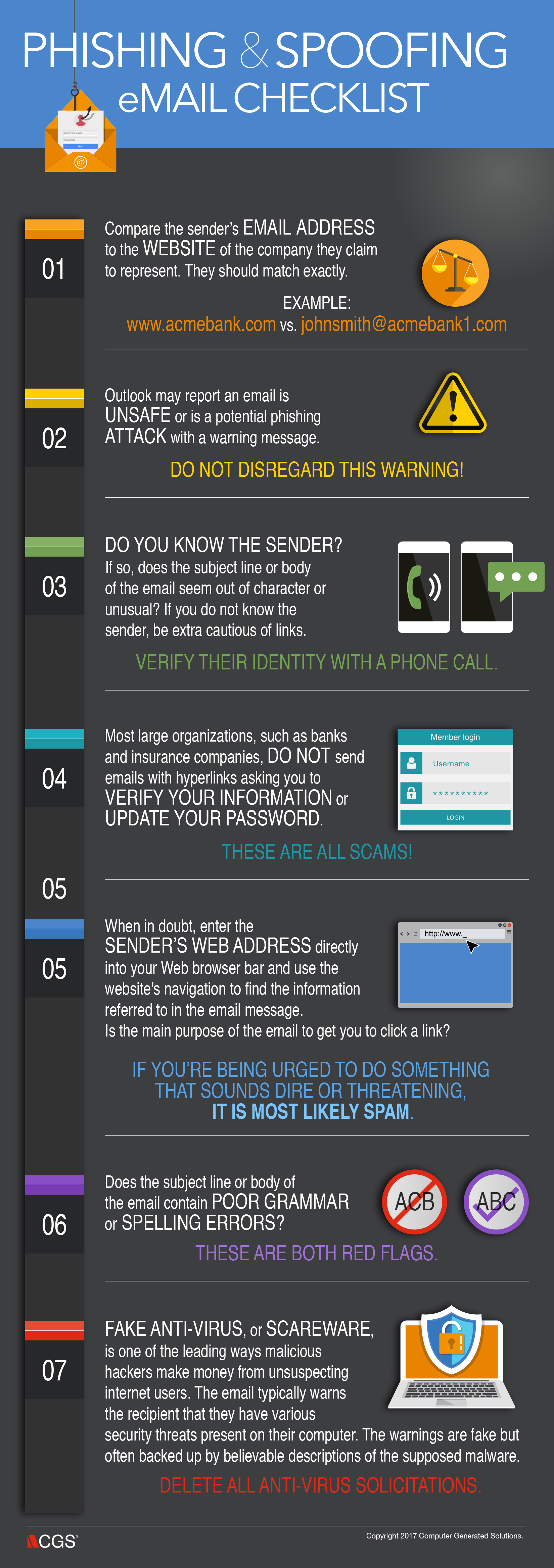
Phishing & Spoofing eMail Checklist

Cyber-attacks can take many forms including attachments that will install a virus, Trojan, or other malware on your computer; links that take you to a webpage that installs malware on your computer; and phishing emails that trick you into providing personal information such as User IDs, passwords, and account numbers to hackers pretending to be trusted companies and sites. Email spam filtering is far better than it used to be, but the best way to defend yourself is to be alert to potential fraud and know how to spot a malicious email. Below is a list of basic safeguards you should know and practice before opening email messages and attachments.
To read more about spotting fake and malicious emails, check out our blog post: How to Identify a Malicious Email: 6 Tips.